How we install Passwd in your Google Cloud Project
Tier: Enterprise
During the setup guide, you were instructed to give us some basic information about your organization and the Google Cloud Project. What do we do with this information? How does the setup work? What can we do with your data after we finish the installation (spoiler: nothing at all)?
Why do we need your Google Workspace admin email address and your domain?
When Passwd runs in your project, it needs to fetch information about users and groups in from Google Workspace. This data is used on the front-end to display readable names of the groups and users instead of IDs or plain email addresses.
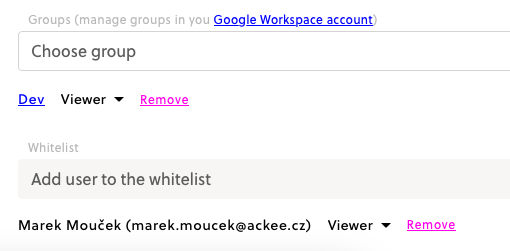
We would love to be able to fetch the data without using your admin email address (or any other address). However, we are limited by the Google API, which requires us to impersonate an admin account. Detailed information can be found here
Control API access with domain-wide delegation - Google Workspace Admin Help.
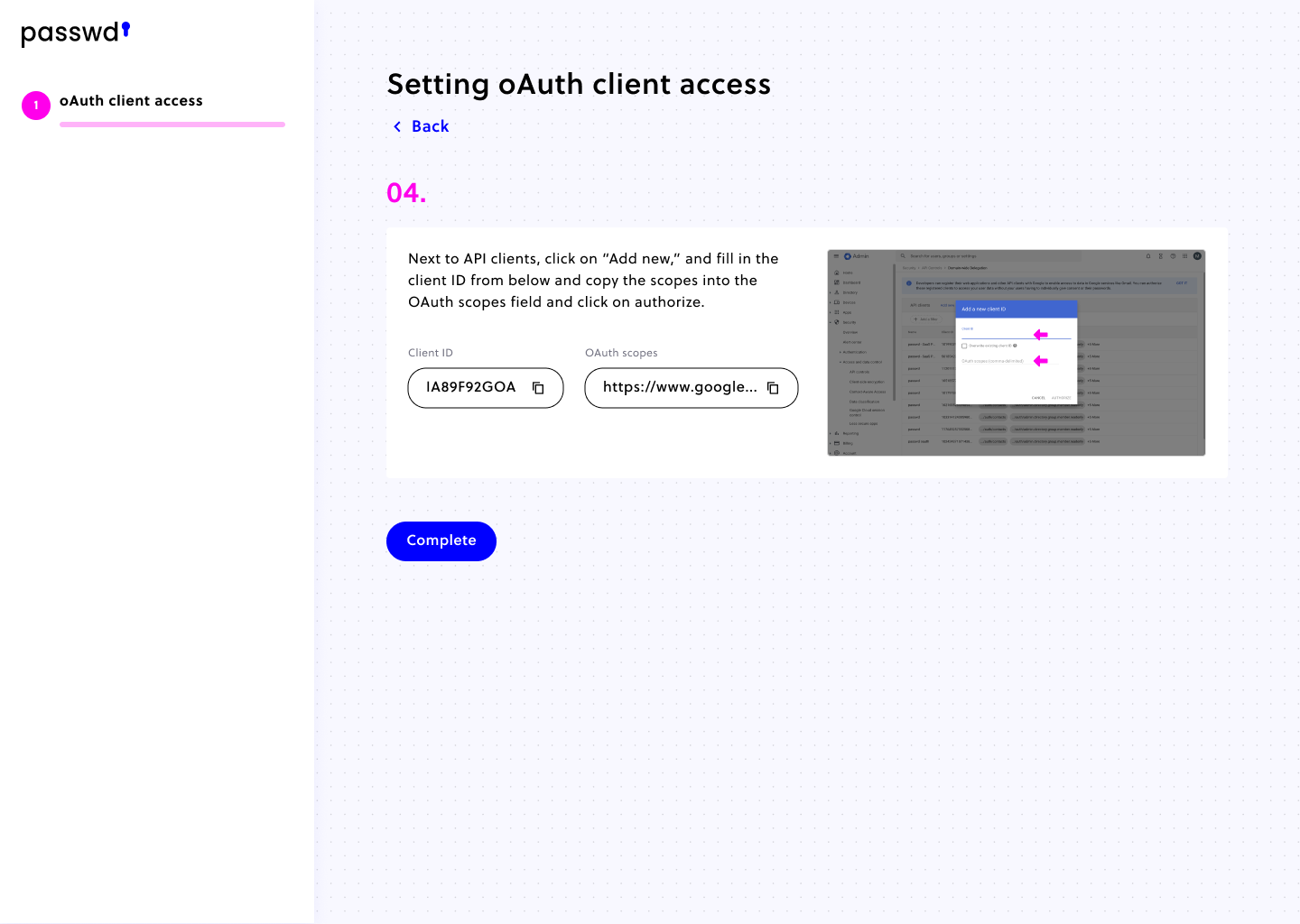
Remember that the app cannot access more than you allow it, which is why we also need you to allow us to access some scopes. And this exactly why the following step is part of the installation guide:
You can learn what these scopes mean here and here. As you can see, most of them are read-only, meaning we can only read data and not modify them. But what about the ones that are not read-only? In short, they are also read-only. They just don’t have the ending 🙂.
What do we change in your Google Cloud Project?
When we get access to your project, we expect a freshly created project with a configured billing account. If it's not the case, we contact you and resolve the issue with you. We then move to make the following changes to your project.
During an installation, we create several buckets (places where we can store files) where we store backups of your data. No one has access to these buckets except you as the owner in GCP and files served to you when you visit [your-domain].passwd.team website.
There are, in fact, a few more, but they are automatically generated by Google Cloud, so we will skip their description.
We also set up a Cloud Run instance and one Cloud Function. Cloud Function is responsible for backing up your data. They are retrieved in their encrypted form and stored in it too. This backup function doesn’t understand the data but copies them to the bucket.
Cloud Run instance is a bit more complicated and it's the backbone of Passwd. It is the backend for UI (it doesn’t matter if it is a web page or an extension). We use Cloud Run because it runs only when you need it to run, but it can also scale up if needed.
And for the backend, we also need a database. We chose Firestore, a No-SQL database developed by Google. This database choice is fast and works great with Passwd, but it is also cheap, and you don’t have to pay for its instance (as you would have to with something like MariaDB or PostgreSQL).
We also need to deliver updates to you. For this, we use a combination of Source Repository (a git repository) and Cloud Build, which together handle our updates workflow.
And lastly, we also use Google Cloud KMS service to generate and store an encryption key to protect your data.
We may need you to change some policies
When installing Passwd in your Google Cloud project, some policies might need to be adjusted to ensure proper functionality. Below are the policies that may require changes:
- constraints/storage.publicAccessPrevention: Required to serve the Frontend code.
- constraints/storage.uniformBucketLevelAccess
- constraints/iam.disableServiceAccountKeyCreation: Passwd needs a service account in order to update your passwd instance without a direct access.
How to Change These Policies
To modify any of these policies in your Google Cloud project, follow these steps:
- Go to the Google Cloud Console.
- Select the Passwd project
- Navigate to IAM & Admin > Organization Policies.
- In the search bar, enter the specific policy constraint name (e.g.,
constraints/storage.publicAccessPrevention). - Click on the policy to open its details.
- Adjust the enforcement setting accordingly.
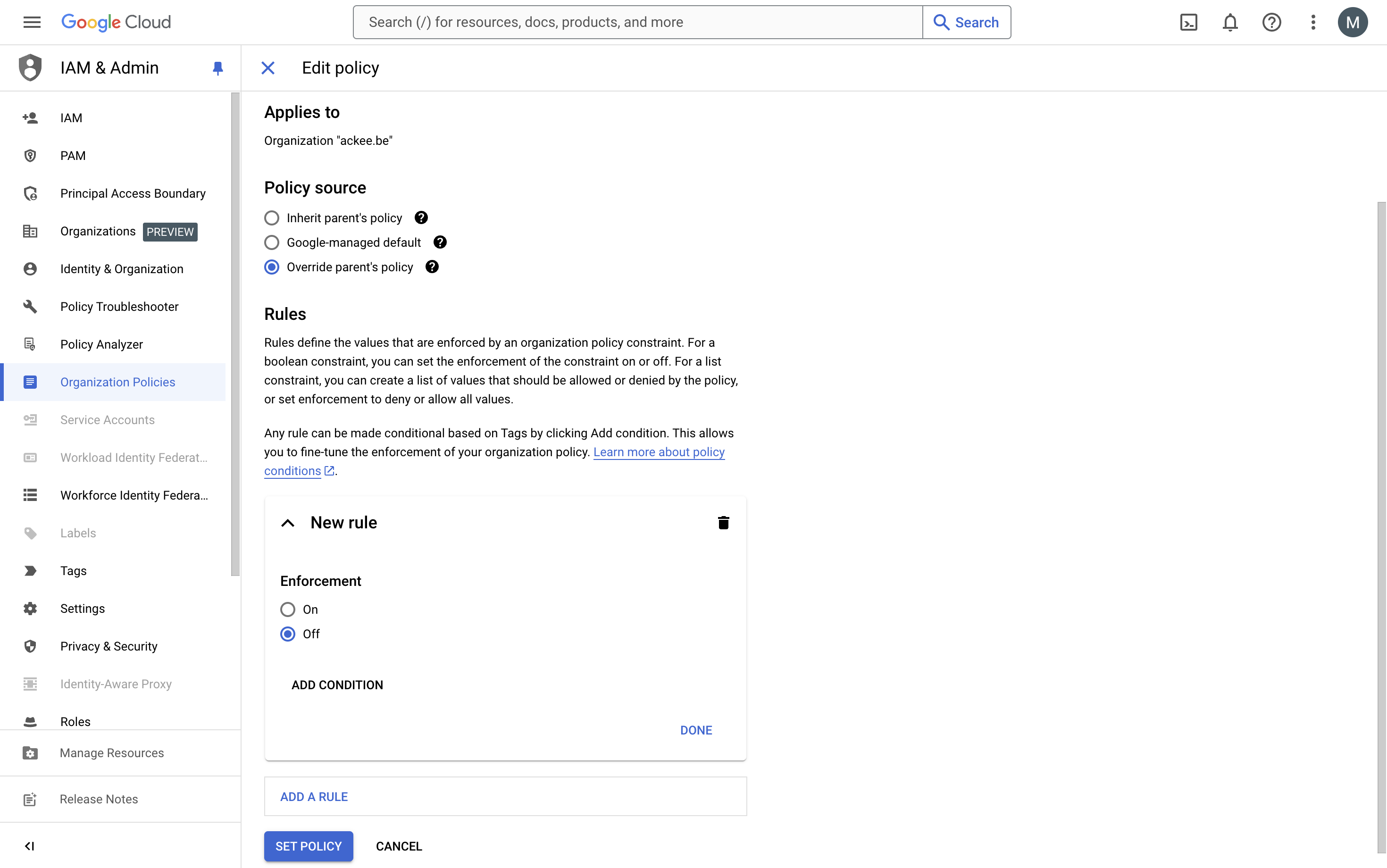
- Click Save to apply the changes.
Ensure you have the necessary permissions to modify organization policies.
I am not able to change the policy
You probably don't have the appropriate permissions.
- In the project picker select and Organization (the one with the office building next to it).
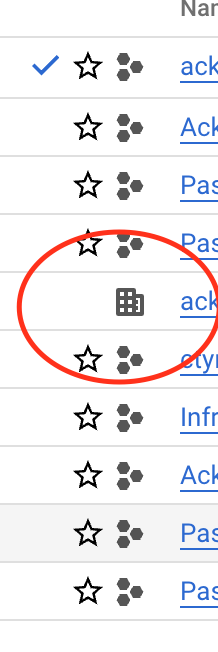
- Navigate to IAM & Admin > IAM.
- Assign yourself the Organization Policy Administrator role.
- Navigate back to the Passwd project and try again.
Can we access your project or data after the installation is finished?
TLDR: No, we cannot.
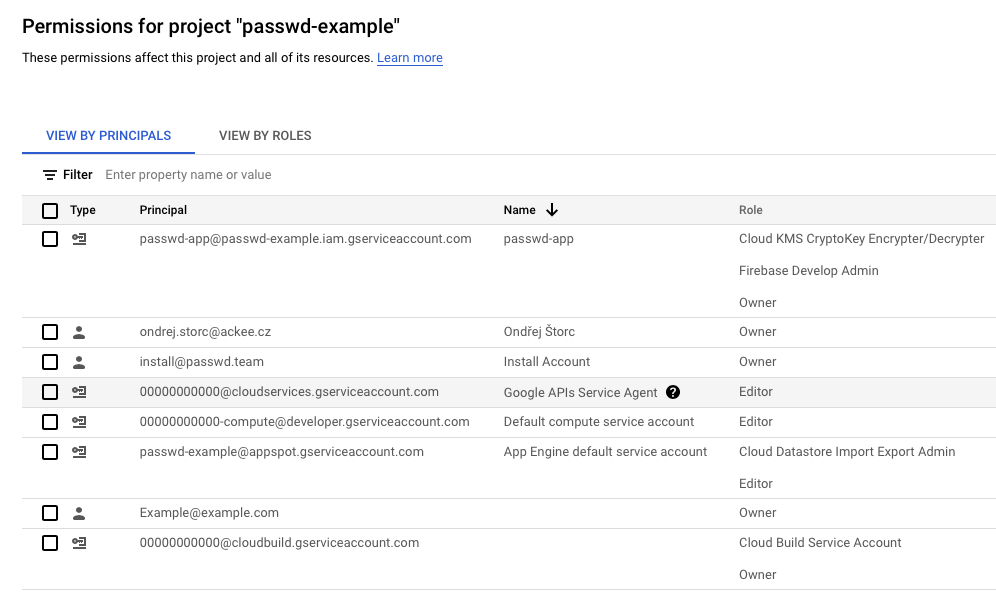
After the installation is finished, we send you the final instructions for the installation. At this point, we still have access to your project and await your confirmation that everything is working. When we get this confirmation, we remove ourselves from the project. What does this mean? We remove our personal accounts from the project (you can check that on the IAM page in Google Cloud).
In the example above, we still have access to the project. Two accounts have access: installation account with email address install (at) passwd.team and person who performed the installation, in this case, ondrej.storc (at) ackee.cz.
Once these two accounts are removed from the IAM page, we lose all access to the project except towards Source Repository, to which we can still push, but nothing else.
Summary
- We need your Google Workspace admin email address and your domain to be able to fetch data about your users and groups.
- To make sure everything works seamlessly, we set up the following features in your GCP: several buckets, a Cloud Run instance, one Cloud Function, a Firestore database, Source Repository, Cloud Build and the Google Cloud KMS service.
- We cannot access your data after the installation is finished and your revoke the access.