Audit log
Tier: Enterprise
Audit log is one of the Passwd’s features that helps enhance overall security and smooths the way for GDPR and SOC 2 compliance. User and group permissions enable you to set restrictions, but auditing informs you about what actions your team members actually perform.
What’s an audit log?
Auditing is a chronological and security-relevant set of records that tracks events and changes. In other words, auditing gives the admin the tool to monitor the activities of the users. GCP project admins (the person who created the project and participated in the installation) can access the audit log in the Logging section of their Passwd project in the Google Cloud Platform administration.
Go to your Google Cloud Platform administration > Your Passwd project > Logging section
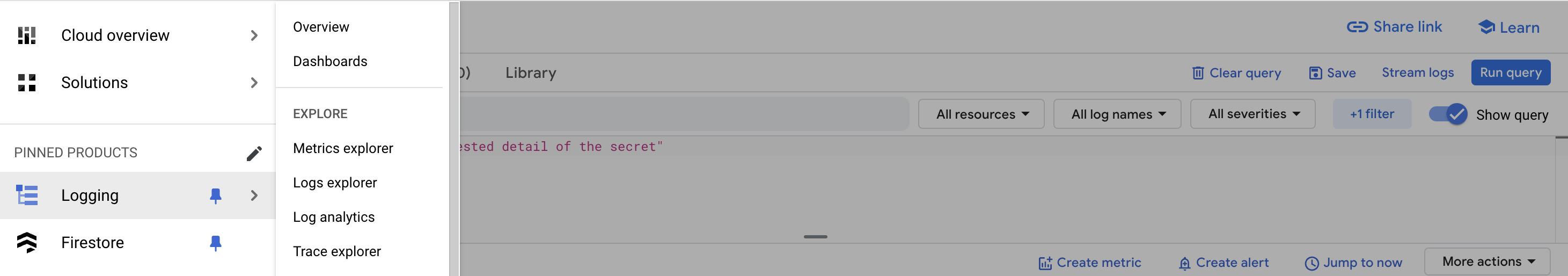
How to search logs
The logs have a fixed structure: the word secret- is followed by the name of the action: create, detail (when someone views the record), update (when someone changes any field of the record) and delete. Using the combination of the prefix and one of the action words, you can easily filter log results and you’ll see user-friendly messages. So if you want to check all record deletions, search secret-delete. If you want to see actions performed with a particular record, search its ID. And if you want to learn more about someone’s activity, use their email address to filter the results. Alternatively you can use the user's email or record's ID
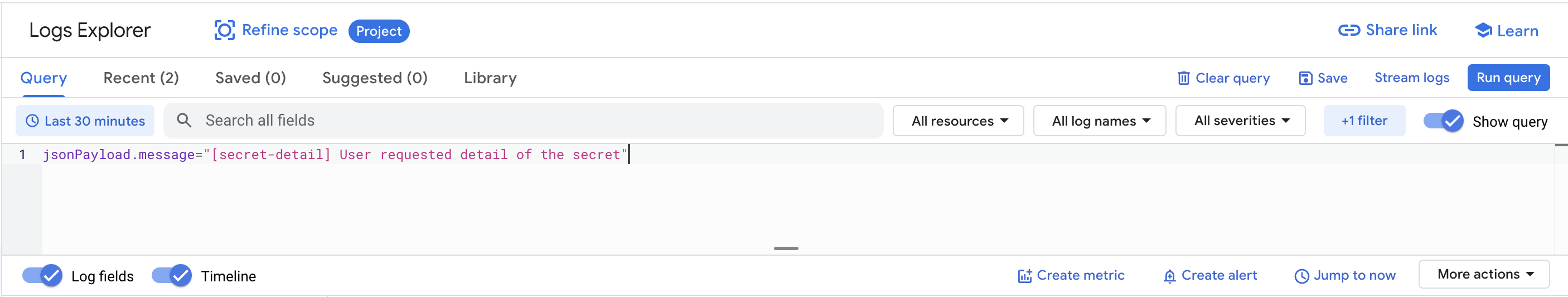
jsonPayload.message="[secret-detail] User requested detail of the secret"
What the logs tell you
You’ll find all the details of the log after clicking on it. You can see that the only part of your secret record we actually log is the ID. For this reason, our auditing is completely safe. Even if someone got possession of the audit log, they wouldn’t get any of your secret information. Plus all audit records are stored in your GCP project that only you can access.
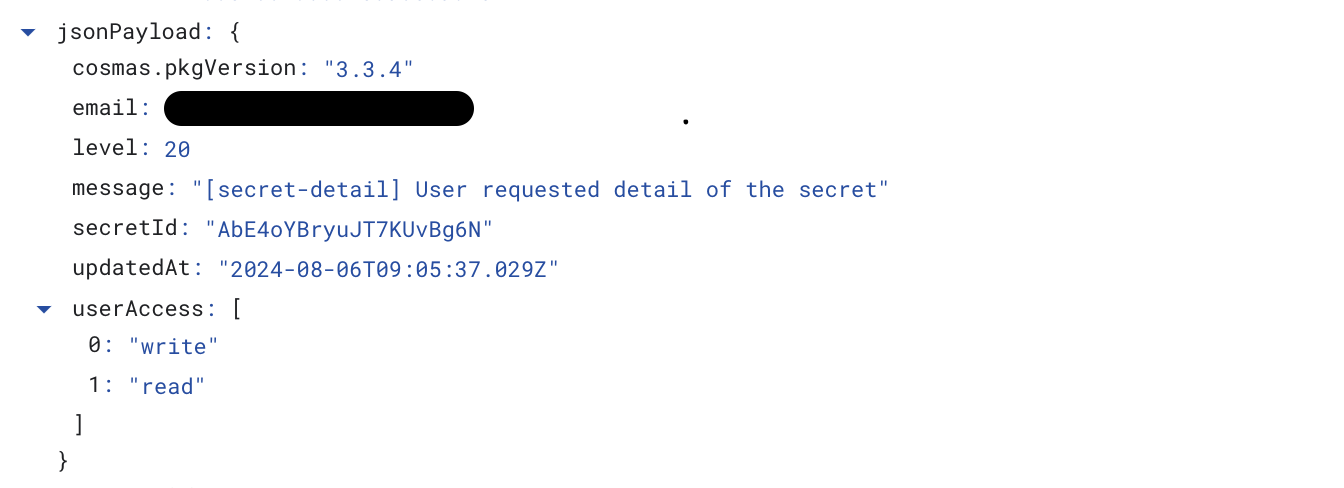
The logged data can be later used to trail activity and generate overview reports using API. But the audit log in Google is a nice and simple tool to monitor what’s actually happening with your sensitive data.